Blog post -
Advice: The risk of malicious social media account takeovers
Social media networks are key for a wide range of micro and small businesses all over the world. Instagram and Twitter have led the changes in marketing and branding for these organisations by providing a platform where they can compete with larger organisations while retaining a ‘craft’ ethos.
More than likely, these smaller businesses don’t have an official IT, marketing or comms department and rely on one or two employees to do everything, including social communications, engagement and networking. This can make them an attractive target for criminals looking to extort businesses by taking over social media accounts that have developed into an important channel of communication, revenue and customer service
What is a social media account takeover?
Social media account takeovers, or account compromise, occurs when someone logs into a social media account and takes control of it without permission.
Sometimes you hear phrases like ‘I had my social media account hacked’. In reality, the accounts probably haven’t been ‘hacked’, but they have been taken over by a malicious individual who has simply guessed the account password, in cyber security, we refer to this as compromised, and the malicious individual as a Threat Actor.
Who does it and what is the motivation for doing it?
- Extortion: the malicious actor who has taken over the account could look to blackmail the legitimate owner, demanding some form of payment before relinquishing control.
- The compromised account can be used for more criminal activities, including payment fraud and phishing campaigns. These phishing campaigns can be very successful as the recipients treat messages from a ‘trusted’ brand or company as being safe.
- The malicious party might simply be looking to cause reputational damage or embarrassment either for fun, or more malign reasons.
How does it happen?
There are several ways to compromise a social media account, the most common ways are to simply find the password in a breach elsewhere, or to guess the username and password for the account. This is made easier where the account owners overshare information which is often used to generate passwords (such as date of birth, pets’ names, hobbies and interests), or where passwords are over-simplistic (such as Password123).
With companies of any size, passwords are often shared between staff and third parties who run these accounts on behalf of the organisation. Passwords are even re-used between different social media accounts. The expense and impact of having complex passwords that change regularly, multi-factor authentication and auditing to confirm who can post can be contrary to the agility of a microbusiness, but using a single password is a great risk to the business’ entire online presence.
If the account password is disclosed due to a breach, then all of the social media accounts are potentially susceptible to an account takeover. Criminals collect and trade lists of compromised passwords, and account credentials are regularly sold at high values in illegal online trading sites, before being used for a multitude of different attacks.
Many social media platforms enable a user to attempt to reset their password via the forgotten password mechanism and only require the username to do so, which is typically the brand name being advertised.
Depending on the contact details available and the user’s security settings, the social media firm may attempt to help the user regain control of an account, often via email or SMS. During the reset process, the user is presented with a heavily redacted version of the email address and the associated mobile telephone number to ensure the requester knows the missing information before issuing the password reset.
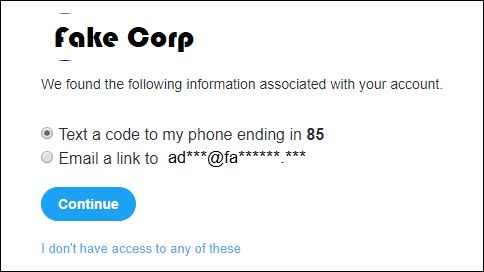
Figure 1 - Example of forgotten password feature revealing partial email address
In combination with other Open Source Intelligence (OSINT) techniques it is often possible to guess both the email address and phone number. If this email address has featured in a breach with a corresponding password, and that password hasn’t been updated since the breach, then it is relatively easy to access the account.
Prevention
By nature, the goal of social media marketing is to ensure the users’ posts reach as large an audience as possible. This insecure configuration can result in the disclosure of information to other users, such as dates of birth, phone numbers, email addresses and other personal information. To make your social media accounts as secure as possible:
- Use a specific mobile phone for social media accounts, with a number that you do not disclose publicly.
- Create and maintain separate email accounts for each account so that the majority of passwords remain secure even if one is disclosed.
- Use a password manager to make it easier to use complex passwords and change them periodically.
- Review any social media accounts to ensure they employ the use of security features such as multi-factor authentication.
- Maintain awareness of phishing attempts that are intended to encourage you to disclose the account credentials.
NCC Group offers several services which help an organisation to understand their digital footprint and online exposure from an attacker’s point-of-view, whilst providing advice on how to mitigate the risks and manage your security and privacy.
Topics
- Consulting