Blog post -
Cloud Responsibility: webinar questions answered
We often get asked about who is responsible for what when it comes to cloud security so we delved into the topic during our latest webinar, Full Speed into the Cloud: but where does the responsibility lie?. Two of NCC Group’s cyber security experts, Mo Louw and Anton Pavlov, explained the responsibilities of end-users and how customers can protect their cloud environment from security threats. Amazon Web Services Cyber Security Partner Manager, Dean Lawrence, joined us to provide insights as well.
A full list of questions and answers are explored in this blog and we hope you find them helpful as you seek to understand and secure your cloud environment effectively.
1. How can we assure leadership that information assets in cloud environments are protected according to the particular risk appetite or tolerance of the organisation?
Assessments and audits are the best tool for providing assurance that a particular level of security is achieved. When NCC Group is contracted for this, we take a look at a number of things, including:
- The organisation’s assets and the related policies, standards and procedures
- How the assets are managed
- The risk management framework the organisation uses
- How that framework is applied
- How threat modelling is progressing
- Specific security frameworks and controls that the leadership wants to align with
- Apply a maturity overlay across the assessment of the organisation’s assets, thereby providing leadership with the assurance of the level of security posture (current and target).
We also provide an organisation with an impartial view of their security posture, information security framework and architecture using international best practice. The final report is then able to provide the organisation with an acceptable level of independent assurance and guarantee on their security maturity.
If you are using AWS, then we also recommend accessing their AWS Artifact self-service portal, which provides free access to all their security and compliance reports, as well as select online agreements. With this information, organisations can perform due diligence on AWS services and continuously monitor how they are performing in these areas.
2. How significant is Data Loss Prevention (DLP) software for data security in the cloud?
If you have the budget to deploy DLP software, then it’s a great addition to your cybersecurity arsenal. However, it’s important to complete due diligence on the software; DLP costs a lot and doesn’t always deliver on its promises. The solutions you’re considering must be tested to ensure that they provide sufficient protection to warrant investing in them.
Interest in DLP has increased after the widely-adopted transition to remote work. DLP covers a lot of different scenarios and first you need to understand what you want protected. If you are concerned with email, consider Office 365 DLP features. If you are concerned with sensitive data discovery, consider Amazon Macie. Regardless of your use-case, DLP depends on effective enterprise data classification.
Another aspect is achieving uniformity of DLP policies across the whole organisation including cloud and on premise assets. Yet another aspect to consider is Mobile Device Management integration with DLP.
3. Do you have any recommendations for DLP solutions for multi-cloud environments?
First you need to identify the use case for DLP, then you need to establish enterprise data classification.
It is quite possible that there is no one size fits all solution.
- Office 365 Security and Compliance Center is designed for Microsoft-centric shared work environments with Exchange, Teams and SharePoint.
- On the other hand, Amazon Macie is targeted towards discovery of static data in S3 storage.
- If you have multiple email streams, consider Symantec DLP that can integrate Gmail and O365 data feeds.
- ForcePoint has a number of products covering different aspects of DLP.
It is important to note that adoption of an external DLP service raises complexity of authentication and access control in the enterprise; by design, DLP solutions have to deeply integrate in the workflow.
4. What are your recommendations on storing encryption keys? Are they better with the customer or the cloud provider?
The answer is “it depends”. Here are a few of the aspects to consider when choosing the encryption model.
- Risk assessment. What is the impact of data loss? What is the impact of data compromise? What is the impact of data made public?
- Compliance requirements. Is there data locality requirement? Are there policies related to cloud storage? Are there policies related to physical key storage?
- Technical requirements. Do you need to operate on data without access to the cloud? Do you need high-availability? Do you need compatibility with CDN model?
In general, encryption keys stored in a cloud service such as KMS allow a very high degree of protection and availability. The access to cloud key storage should be integrated with Enterprise access control. Key management is enforced in line with Enterprise policies. Therefore, it is preferred to store keys in the cloud.
On the other hand, requirements for data access may make cloud key storage impractical. In such cases key storage has to be implemented in some other way.
It should be noted that key storage in the cloud is well-understood and it is a compulsory part of cloud audits.
Risk of custom key storage solutions is not well understood. It is recommended to review the risk and perform a penetration test of such a solution.
5. When personal information is stored in the cloud, does the customer need to be certified in ISO 27001 and ISO 27018, or is the provider’s certification and alignment with the regulations sufficient for compliance?
It’s good for both the provider and the customer to be certified and align with government recommendations where possible. Each is responsible for different aspects of security in a cloud solution and therefore must meet any requirements and follow best practices in their respective areas.
However, while it is good to be certified, don’t fall into the trap of assuming that certification is all you need. It’s necessary to approach cyber security from both ends: management, government reporting and compliance, paired with a solid understanding of your data flows and data architecture. And everytime you adopt a new platform or an update occurs, this may affect your security. So certification is not a one and done security activity.
6. What are your recommendations for someone wanting to learn more about cloud security and get certified? Are ISC2 or vendor-specific certifications better?
Having a certification is definitely a plus, however, it does not provide an insight as to how you work in a team, nor your ability to communicate to stakeholders on various levels (and not only technical people). Experience in the security field can be just as valuable as a certification. Many security professionals work their way up from admin roles to engineering, then onto architect roles.
With a vendor neutral certification, e.g. CCSP and CISSP, the candidate shows that they are proficient in their understanding of security and the cloud, which can be applied across multiple environments and not only in the cloud or for a particular cloud service provider. A vendor-specific certification shows a greater depth of proficiency with a particular cloud service provider (CSP) that would be valued by most organisations, as many are already migrating to multi-cloud environments. Once you have a certification or demonstrated proficiency, you can look into specialities such as SABSA Advanced Architecture and Design.
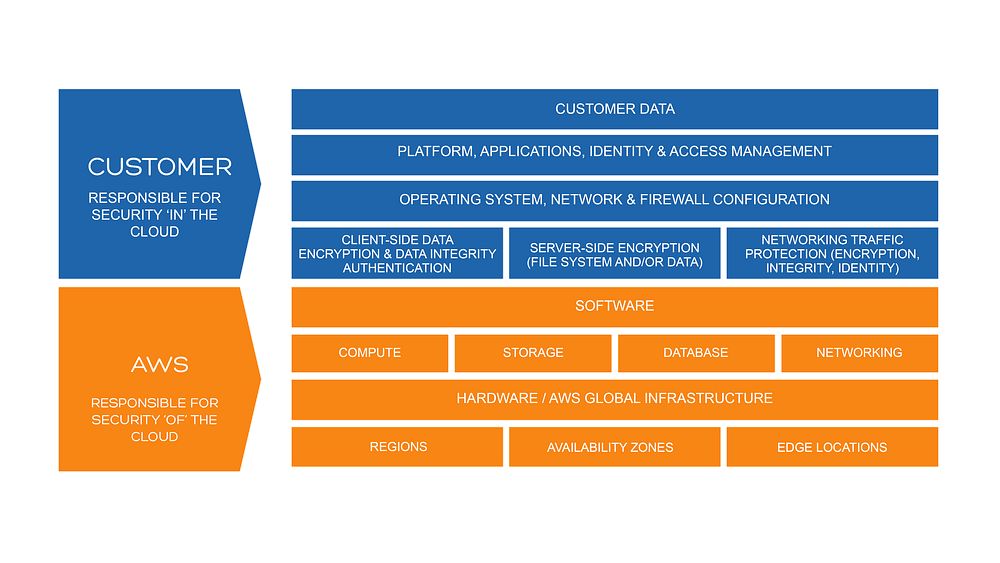
7. Does most of the underlying security of a cloud system lie with the provider?
This answer to this question comes down to the service that your provider is implementing. For example, in serverless cloud models, AWS assumes a lot of the responsibility for the system’s security. But where a virtual server exists, the customer assumes more responsibility as they have the capacity to add to the operating system. In other words, where the provider goes above the line providing more capability (see image above), they take on more responsibility, but where they do less, the customer has more.
Another example is the storage of personally identifiable information (PII). The provider will be responsible for the security of the storage solution, but the customer is responsible for the movement and management of the information.
8. What is your view on Cloud Access Security Broker (CASB) solutions?
CASB shifts the trust zone border from web-end points. CASB knows the protocols of SaaS applications, so it acts as a traffic control with deep packet inspection capabilities.
Arguments in favor of CASB:
- Allows connectivity of untrusted devices including BYOD
- Fast roll-out
Arguments against CASB:
- Potentially many CASB providers are required to cover all cloud applications deployed so the costs can quickly add up.
- CASB masks web application vulnerabilities. Enterprise with CASB can devolve to a hard-shell security model. This can be disastrous if CASB is removed or bypassed.
- CASB providers have access to data. This may be an unacceptable risk for certain data classes.
You should evaluate the use-case for CASB and analyse other aspects (time frame, costs, BYOD policy). CASB is good as a complimentary service, but should not be relied upon as the primary defense.
9. How much should a small company invest in cloud security?
We recommend investing as much time and resources in security as you can, taking into consideration your industry and compliance requirements.
If you’re wondering where the first place to start is, then it should be your people. They are your best investment. Access permissions and roles are one of the most important security measures in the cloud. If you have good people working for you, who understand and follow the processes you have set up, then they will help you maintain a secure environment. Training them in cyber security best practices and educating them on threat models will go a long way towards reducing risk.
While your first investment should be your people, your second should be your documentation. Each organisation will have to choose how much they’re willing to spend on documentation. This is where third-party providers can be a good option for small businesses to augment their own resources. You might not have the in-house capabilities, but you can bring in external security advisors to provide a policy pack or conduct an audit of your system.
Cyber insurance is another area where you should consider investing. Once you have a full understanding of your assets and their value, you can determine what level of insurance you need.
Ultimately, though, your organisation needs to make the call about your risk appetite and the controls you want to implement to appropriately secure your assets to decide how much you need to spend.
10. Why do you think cloud adoption has been faster in non-APAC regions, especially by banks and fintech?
It’s difficult for us to comment on non-APAC regions because most of our experience is here. Some potential reasons could include how other countries think about data sovereignty, or the impact of the Australian Royal Commission into banks is shifting the focus away from cloud expansion temporarily. The Australian Signals Directory has also ceased publishing the Certified Cloud Services List (CCSL), which may have caused some hesitation in companies.
However, in the last two to three years, we’ve seen a fundamental shift in APRA’s opinion of cloud services. As the regulator has grown in their understanding of the cloud and as cloud services and security have developed, there is much more openness to this technology. This has been a strong catalyst for the digital innovation we’re seeing in the banks and fintech industry now.
To understand how NCC Group can help you to assess and ensure the security of your cloud environment, get in touch by emailing apac@nccgroup.com. If you’d like to watch the entire webinar, where Mo, Anton and Dean take a deeper dive into the topic, you can access a recording of the webinar here.
Topics
- Consulting