Blogginlägg -
When the attack has taken place, it is too late to talk to your board
In order to get the buy-in from your board of directors, they must understand the importance of cybersecurity, from the design phase up to the response phase. Only then will they include it in their overall strategy. But, how to get them involved? After all, the board consists of very different profiles.
As your time and that of your board is very valuable, you need to need to be concise. This is key. Furthermore, I want to offer you the following tips:
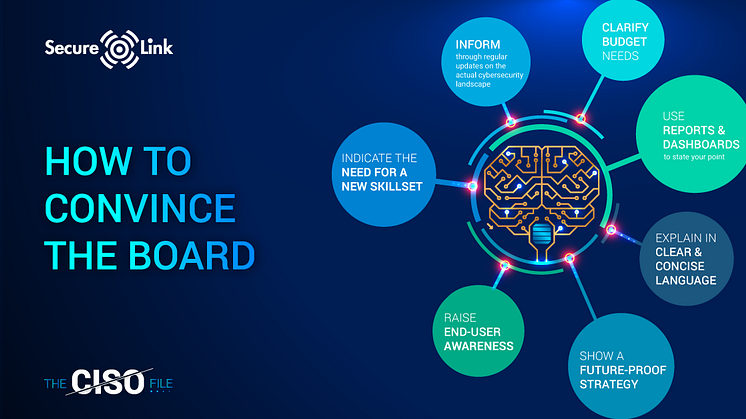
9 tips to convince your board
- Give them regular updates (e.g. every quarter) regarding the actual cybersecurity landscape
E.g. the top 3 core security risks in your business - Use reports (no more than 10 pages) and dashboard information to state your point
E.g. show them the overall status of security framework compliance (ISO270001, NIST, CIS TOP 20, etc.)
E.g. demonstrate the loss of resources or downtime due to security incidents over the last quarter - Explain everything in very clear language. This means avoiding jargon and including simple metricsE.g. If scenario X happens, loss = 5 million or risk level is red (critical)
- Be transparent about your choices, strategy, and plans and use clear examples
- Clarify your budget needs. The only way to get your budget is to get them engaged
- Inform them on your current cybersecurity strategy and make sure to show them it is future-proof
- Define how you will raise end-user awareness to make sure security becomes part of your company culture
- Show them you have the right skillset in your team or indicate the need for finding other profiles or outsourcing (parts of your) security
- Describe the current security maturity level of the organization and how you are doing compared to peers.
How SecureLink helps you convince the board
These nine tips are of course easier said than done. To assist you in convincing the board, we offer the following services:
Security Reports & dashboards
Becoming more mature regarding cybersecurity often implies continuous reporting to the board upon security risks. The investments you make to avoid these risks, need to be ‘measured’ (ROI).
To offer the correct reporting to your board, you need to:
- Translate technical risk into business risk and potential impact
- Justify new security investments
- Have a single view on the company’s security status, combining on-premise, cloud, and endpoints
- Show compliance to auditors
SecureLink acts as a trusted advisor and helps customers build the required dashboards and reports. We provide SecureLink packages that contain predefined dashboards and reports and customize them to your business goals when required.
To do so, we collect the relevant information from our security solutions and integrate them into a single platform and build real-time dashboards on top. The SecureLink team is there to help you analyze the data when required and to help you take strategic, future-proof decisions.
Security Maturity Assessments
The Security Maturity Assessment helps you understand which improvements to your cybersecurity operations should be prioritized and why.
Through in-depth, interview-based workshops, a maturity level is assigned in the area of people, process and technology. You will get an executive report and a summary of your results. You will have insights into your gaps, weaknesses, and risks.
Furthermore, you will get recommendations for improvement in a clear action plan which will enable you to prioritize improvements to your security strategy, so you can maximize the outcome of your investments into cybersecurity.
Learn more about SecureLink's Security Maturity Assessment here.
Outsourcing IT Security
Thanks to the Managed Security Services of SecureLink, you can rely on proven security expertise, even on a 24/7basis if necessary. You can focus on your core business while our team of highly-skilled experts in combination with solutions from leading technology vendors are extending your security operations. By opting for Managed Security Services, you will have lower and more predictable costs and access to a large team of experienced analysts.
Author: Katrien Anthonis



