Blogginlägg -
Innovation or proven-value? What to choose?
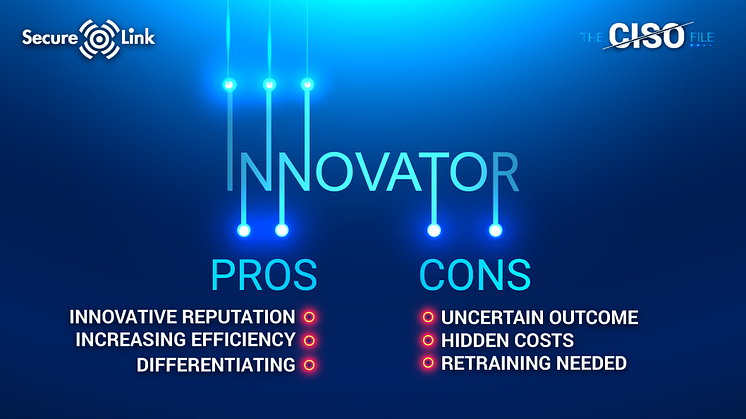
The pros and cons of being an innovator
Some companies always have the need to innovate. Just think of high-tech hospitals, financial institutions or other businesses that work with extremely sensitive data. When the board realizes the importance thereof, they will allocate the budgets. But, what about your company?
In short: Does your business want to be the first to try it? Or do you want to see the evidence first?
Being a pioneer has multiple advantages. Just think of:
- Attracting many employees and customers because of your innovative reputation;
- Increasing efficiency
- Differentiating from competitors
But, it can also have less fortunate results:
- You can’t precisely predict the outcome
- There might be hidden vulnerabilities, resulting in hidden costs
- There is no proven value
- You might have to retrain your employees, resulting in additional expenses
- No concrete planning is possible
An example: SIEM or AI?
The world is digitalizing, and businesses are challenged in many ways. When it comes to cybersecurity, CISOs often doubt whether they should stick to their SIEM technology or opt for Artificial Intelligence.
Let’s compare:
SIEM
- Great proven value
- Takes much time to set up, often a couple of months
- No loss of data when maintaining
AI
- No real proven value yet
- Takes only a couple of days to set up
- Finds vulnerabilities that SIEM can’t find
- Offers more visibility into what is happening on your network (security-related)
- Less maintenance needed, but you might lose data
SecureLink advises you to test both technologies simultaneously. This can be done through a Proof Of Concept. That way you can decide if you want to replace your existing technology with AI, to keep the old one or to add AI as an addition to the current technology in the form of User Entity Behavior Analytics (UEBA) for example.
SecureLink’s advice on pioneering
To some companies, 1% of extra security is crucial. Pioneering is in their DNA, and they are not afraid to test new technologies, in a safe way. In a safe way means: testing new technologies simultaneously with the older ones. We highly recommend this. As every environment is different, results might be different too. So, you never know what the exact results will be for your business unless you test it through a Proof of Concept for example.
A new solution might be the cutting-edge layer on top of your existing layers. Adding AI, for example, might give you more insights and visibility. Visibility that can be essential.
Companies with less risk appetite may prefer stability when their data is not extremely sensitive. Technologies that have proven value will allow you to precisely predict your results, the costs and timing.
Besides, budgets, sales cycles, and other business protocols might keep you from investing for a while. When you doubt, or when it is not crucial, you can wait for 1 or 2 more years to implement it. Innovative players are often caught up quickly by competitors or acquired by them.
Author: Peter Beerten